
About a month ago (10 November 2021), I got my OSCP certification.
OSCP stands for Offensive Security Certified Professional. It consists in a 24-hour proctored exam to compromise 5 machines.
The only initial information is their IP addresses.
Once these 24 hours have passed, we have 24 hours left to write a report describing the steps that allowed us to gain access to each target as a high privileged user (administrator). The report should contain the discovered vulnerabilities, their severities, a brief description on how to fix them as well as exploitation code.
To prepare for the exam, Offensive Security gives you access to a lab (with more than 70 machines) with different options depending on how long you want to access to it.
A week before taking the exam, I felt that I wasn’t ready. Finally, I got the OSCP at my first attempt 🎉.
Table of contents
- 🤔 General thoughts about the certification
- 🧑🏫 Recommendations for OSCP aspirants
- 🧑🎓 My personal journey
- 🛣️ What’s next?
- 🎁 Scripts, cheat sheet and templates I would like to share
- Some interesting links
🤔 General thoughts about the certification
Although many people interested in infosec want to get the OSCP, it remains an entry level certification. More advanced certifications could be OSEP or OSWE.
The course is huge (850-page PDF course guide, 17+ hours of video) and covers a wide variety of penetration testing fundamentals (enumeration, looking for unpatched services and/or applications, modifying exploits, privilege escalation…).
Going through the lab will allow you to approach more advanced concepts than those necessary for the exam.
Indeed, the lab contains over 70 machines in different networks. This implies that you have to perform port redirection, tunneling, pivoting, lateral movement and so son. Many machines are part of a chain (they have dependencies on each others) so post-exploitation is as important as gaining an initial foothold.
It’s all about developing an intuition and a methodology for the exam and your future security assessments.

The exam is not that hard, since you know there are vulnerabilities and probably public exploits. ExploitDB and Google are your friends. Think also about common misconfigurations or capabilities that can lead to code execution!
I had OSCP in mind for a few years now, but I was discouraged by people telling me that security certifications were useless.
Ultimately, I do believe that technical certifications are not necessary in our field but they can be beneficial in that they allow people to set a goal and ensure that some time has been spent studying very specific concepts.
Disclaimer: Here, I am not talking about certifications based on multiple choices questionnaires.
Keeping in mind that certs remain recognized in our profession and that they are HR filters.
Overall, I really enjoyed my OSCP experience and definitely learned a lot throughout the journey.
When you laugh at infosec certifications, you indiscriminately also laugh at passionate people that have been hustling for years.
— Wim "The New Normal" Remes (@wimremes) October 1, 2021
Is a cert required? No. Does it often help people to set goals and work towards them? Hell yes. pic.twitter.com/glyVrZoJJA
🧑🏫 Recommendations for OSCP aspirants
Build your own Cheat Sheet while doing your preparation, the PWK lab and course exercises, so you can easily copy and paste useful commands. My personal cheat sheet is available here 😉
Don’t be ashamed to use the student forum if you went through every tactics in your cheat sheet/methodology. You don’t know what you don’t know!
Offsec has recently added 5 retired OSCP exam machines in the IT network of the PWK lab. Make sure to do them before the exam.
Read reviews on
r/oscpand various blog posts. You can really benefit from the experience of others (success and failure stories, tools and methodology…).Do not do all the course exercises except you have A LOT of time! Focus only on parts that you’re not familiar with (Antivirus Evasion for instance). Even if I was familiar with most of the concepts and tools mentioned in the course, it took me almost a month to finish them.
Take effective notes using whatever tool suits you (Notion, Cherry Tree, Obsidian, Markdown files in VScode and so on).
Write scripts that can automate your enumeration and prepare a skeleton script for the Buffer Overflow machine (this second advice is no longer valid considering the 2022 exam update).
My Tiny Enumeration
TmuxOrganizer Scripts (TETOS): https://github.com/amirr0r/TETOS
My buffer overflow skeleton exploit: https://github.com/amirr0r/notes/blob/master/Infosec/Pwn/shellcode-stack-buffer-overflow-exploit-skeleton.py
🧑🎓 My personal journey
🎒 Background
I’m 23. At 18, I started to learn about computer science (programing, database management, networks, etc.). I spent a year as a developer in apprenticeship and 3 years as an apprentice cybersecurity engineer focused on embedded systems.
Apprenticeship consists in switching between studying in school and working at a company for a short period of time during one or many years. It could be 2 days a week or 1 month at the company and 1 month at school. During school holidays you have to work at the company, you are a real employee.

Now that I have the certification I think that I was quite able to pass it several years ago if I did not procrastinate so much (but maybe it’s just a bias). However, I am glad that I have passed it this year as I was able to benefit from the course update of 2020.
🥼 Preparation and PWK Lab
Before jumping to the OSCP, I went through a preparation plan to learn about basic enumeration and exploitation as well as file transfer, upgrading shells, Linux and Windows privilege escalation famous methods. As you can see in my blog post “How do I prepare for the OSCP?“, I didn’t complete all the things I planed 🤷. It took me several months since I was working and studying at the same time and I wrote write-ups for (almost) all the machines I did from HacktheBox, Vulnhub and Tryhackme.
I “really” started on September 10th. In September I compromised about 30-35 machines, did all the Big Four and unlocked the IT Department Network. During October, I completed all the course exercises, watched all the videos and I have read the entire PDF even though I was familiar with the most of it because of the preparation. The reason was: I didn’t want to miss any small tricks I could benefit from.
From the end of October to the beginning of November, I compromised more than 20 machines (including the 5 retired OSCP exam machines) then I passed the exam.
After taking the exam, I continued to attack some machines resulting in 58 compromised machines at the end of my lab access. Unfortunately I didn’t compromised all of the 70.
⌛ Exam Timeline
➡️ 14h - 14h56: My exam started approximately at 2 PM (got some issues with proctor software). I finished the Buffer overflow machine within an hour while running enumeration scripts in the background for each target.
➡️ 15h - 15h48: I took a small break then I decided to attack the 10 pointer machine. “Luckily”, I identified the exploitation path very quickly. After completing it, I took another break.
➡️ ~16h10 - 18h45: I looked at the output of my enumeration script to find some low hanging fruits. Decided to go through two machines simultaneously. After almost 2 hours, I got a low privileged shell on a 20 pointer machine then I went to another break.
➡️ ~19h - 20h17: Finding the privilege escalation method was pretty straightforward, while the exploit was running I jumped to the other machine. Finally, I went back and saw that I became the super user 😎
➡️ ~20h30 - 22h53: I fell into many rabbit holes until I found a way to execute code on the remote machine. Yes! Now I just need to find a way to privesc in order to obtain more than 70 points required to get the OSCP. I took a longer break of approximately 1h30-2h to walk outside and come back with a resting mind.
➡️ ~00h30 - 03h06: Since my shell wasn’t stable I used my Meterpreter bullet to upgrade my shell. I also wanted to ensure that I will be able to reproduce each steps for the report so I reverted the machine and I did it once again. Privilege escalation was very obvious but I took many hours to try different ways listed in the privesc enumeration script. If I write the report correctly, I must have 75 points and get the certification 💪!
After that, I left the screen immediately. I went to sleep approximately at 6h30 then I woke up at approximately at 12h. Until the end of the 24 hours exam, I tried to attack the last machine (the 25 pointer one), I found some vulnerabilities but no way to gain a shell.
📝 Writing the report
I used Notion to take all my notes while doing the lab and the exam. Previously, I was used to put everything in markdown files, editing them via vscode and backup them to Github’s private repositories.
In addition to all of its great features, one of the main reason I chose this application is because its faster to copy and paste screenshots from Vmware (via deepin screenshot) to a Notion web tab. Plus, I could always export my notes as markdown files and / or PDF if I wanted to go back.
By the way, I asked Offsec before doing this. Here is what they respond to me:
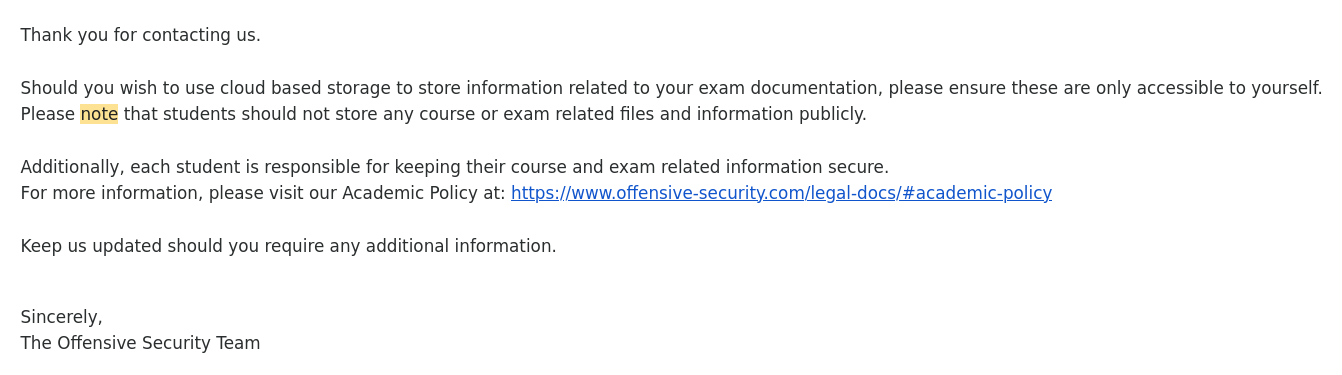
I wanted to use noraj’s OSCP Exam Report Markdown Templates but having been too slow to start writing the report, I ended up generating a PDF from Notion directly.
✉️ Getting the certification
Approximately 24 hours after finishing the exam, I received the awaited email telling me I passed the exam from the first attempt!
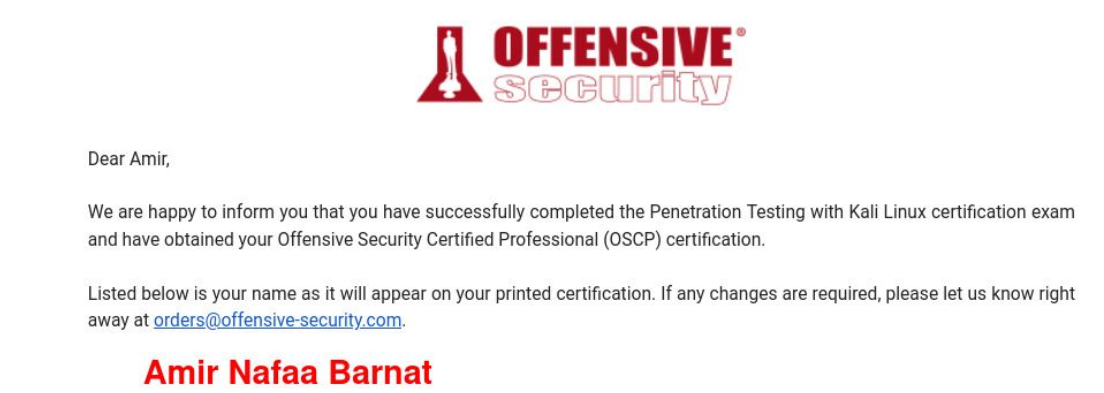
Note: The paper certificate should be delivered within 60 days after passing the PWK exam.
🛣️ What’s next?
- Going through the “Red Team Ops” course form Zero-Point Security and becoming a CRTO (Certified Red Team Operator).
- Completing TCM and Sektor7 courses.
- Playing with HackTheBox Pro labs: Dante, Rastalabs, Offshore, Cybernetics, and APTLabs.
- OSEP, OSWE, OSED and OSWP
- Improving my Reverse Engineering skills via Zero2Auto course
- Taking a look at Blue Team Labs and Cyber Defenders
- Joining a CTF team such as OpenToAll
- … Master of Pwn 😁
🎁 Scripts, cheat sheet and templates I would like to share
One of the things that never ceases to impress me is how much the infosec community shares knowledge: techniques, free tools, free trainings, advices for students as they learn.
📚 Notion templates
https://amplified-maize-ada.notion.site/PWK-OSCP-Templates-11e2f9f66b9e47398cf8ca7d7a9ab8c6
📋 Cheat Sheet + Scripts
- My Personal Cheat Sheet: https://github.com/amirr0r/notes/blob/master/Infosec/boot2root-cheatsheet.md#boot2root-cheatsheet
- My Buffer overflow exploit skeleton: https://github.com/amirr0r/notes/blob/master/Infosec/Pwn/shellcode-stack-buffer-overflow-exploit-skeleton.py
- My Tiny Enumeration
TmuxOrganizer Scripts: https://github.com/amirr0r/TETOS
Thank you for reading me, do not hesitate to hit me on twitter if you have any questions!
Some interesting links
- 0xconda - OSCP Prep Videos
- Rana Khalil- My OSCP Journey — A Review
- Andy Li - OSCP Complete Study Guide
- John Hammond - 100% OSCP: Offensive Security Certified Professional
- John Hammond - 2022 OSCP EXAM CHANGES - Goodbye Buffer Overflow, Hello Active Directory
- Busra Demir - OSCP Prep Youtube Playlist
- Retour d’expérience sur les certifications de pentest OSCP et OSWE - Zeecka
- Acknack - Une expérience OSCP plutôt détaillée…
- Reddit
r/oscp

